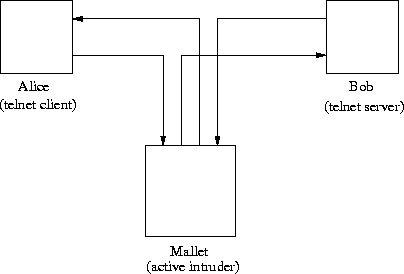
Figure 2.5: Active attack
This type of attack requires the attacker to be able to transmit data to one or both of the parties, or block the data stream in one or both directions. It is also possible that the attacker is located between the communicating parties. See figure 2.5. In this case the attacker can stop all or parts of the data sent by the communicating parties. This attacker can e.g. try to take the place of the client (or server) when the authentication procedure has been performed. Without integrity checks of the received data, the server will not detect that the origin of the data is not the authenticated person. A clever programmer can, with not to much effort, implement a system like this on a computer acting as a gateway (bridge) between two subnets. (On the Internet there are thousands of these computers.)
The following are examples of different attacks this person could impose.
The man-in-the-middle-attack is an attack where the intruder sits in the middle of the communication link, intercepting messages and substituting them with his own messages. In this way, he tries to fool the parties to believe they are talking to each other directly, while they really are talking to the attacker him-selves.